How businesses should be protecting themselves from cybersecurity threats in 2025
The tools cybercriminals use in 2025 are more advanced than ever, making it critical for businesses to avoid even the smallest slips in their digital hygiene. From large-scale data leaks that expose sensitive customer records to ransomware locking down your entire system, the threats facing companies today have real-world consequences that can disrupt operations, drain finances, and damage the trust you’ve built with your customers.
Ooma understands the importance of secure communication in keeping your business running smoothly, which is why we’ve put together this approachable and actionable guide to help your company stay ahead of the most common cyber threats in 2025.
What is cybersecurity?
Cybersecurity refers to the practice of protecting systems, networks, and data from digital attacks. These attacks may involve the theft of data, phishing scams, or the installation of ransomware or malware. They can be motivated by financial gain, espionage, disruption, or, more rarely, as a prank. Cybersecurity involves a range of strategies, including securing networks, encrypting data, training staff, and monitoring for threats.
These days, businesses consider cybersecurity to be a core part of risk management, with global spending on the issue expected to exceed $1.25 trillion in 2025. While this number might sound surprising, cybercrimes are expected to cost the global economy nearly ten times that amount this year alone. The average cost of a data breach is now nearly $5 million, and that doesn’t account for the loss of reputation or revenue, as well as the fines that often result from a data breach.
While all businesses face threats, some sectors are targeted far more frequently than others. Based on global incident data from 2000 through 2025, the most targeted sectors include:
- State institutions/political systems: 51.78%
- Critical infrastructure: 41.73%
- Corporate targets: 15.14%
- Social groups: 6.17%
- Media and education: Around 6% each
Among critical infrastructure, attackers most often target healthcare, finance, telecommunications, and transportation. These sectors are vital to daily life and economic stability, making them high-value targets for cybercriminals and nation-state actors.
Every click, download, and message carries some level of risk, which is why cybersecurity services have become the mandatory safety net businesses need to operate confidently.
What are the most common cybersecurity threats for businesses?
Today’s cyber threats are more targeted, deceptive, and destructive than ever, and they’re not limited to only large enterprises. According to the Small Business Administration, nearly 88% of small business owners believe their company is vulnerable to a cyber attack, and this concern appears to be justified. Some of the most common types of cyber threats businesses face include the following:
- Phishing refers to fraudulent emails or messages designed to trick employees into revealing passwords or sensitive data, such as credit card information or Social Security numbers. This information is used to steal money and identities, as well as send spam from compromised email accounts.
- Ransomware is malicious software that locks access to files or systems until a ransom is paid. It often occurs due to successful phishing scams or through downloading infected programs.
- Malware is a broad term for software designed to cause damage or gain unauthorized access and is often spread through the same means as ransomware.
- Data breaches occur when unauthorized individuals gain access to confidential or sensitive information, opening the door to theft or ransom attacks.
- Denial-of-service (DoS) attacks occur when a server or network is maliciously overloaded, making it unavailable to users. This is usually accomplished through flooding a network or host with traffic until it crashes or can no longer respond to organic traffic. This delay in service can be costly for companies in terms of lost sales and weakened customer trust.
- Insider threats are employees or contractors who compromise security through accidents, negligence, malicious intent, or collusion.
Cybersecurity advice for businesses in 2025
As always, the best defense is prevention, which requires awareness, consistency, and routine. In the office, employees should be educated and trained to recognize phishing attempts and avoid risky behaviors, such as downloading infected programs or clicking on unknown links or files. Additionally, all employee devices should have up-to-date antivirus software installed.
On the more technical side, you can reduce risk by using firewalls, encryption, and private Wi-Fi networks to keep sensitive data secure. Additionally, consider limiting access to certain information based on which roles require it, and keep a close eye on user accounts. Passwords should be updated regularly, and it doesn’t hurt to add multi-factor authentication for any locked-down systems or accounts.
Finally, redundancies and backups can be the difference between a quick fix to a breach and a catastrophic, lengthy shutdown to your operations. If you don’t have an in-house security team, working with the right providers can go a long way to keeping your business secure.
As overwhelming as cybersecurity may seem, it can be managed through building habits, staying alert, and providing your team with the tools to respond quickly.
At Ooma, we help businesses stay connected, and we take that responsibility seriously. Our communication systems are built with security in mind, so you don’t have to choose between ease of use and safety.
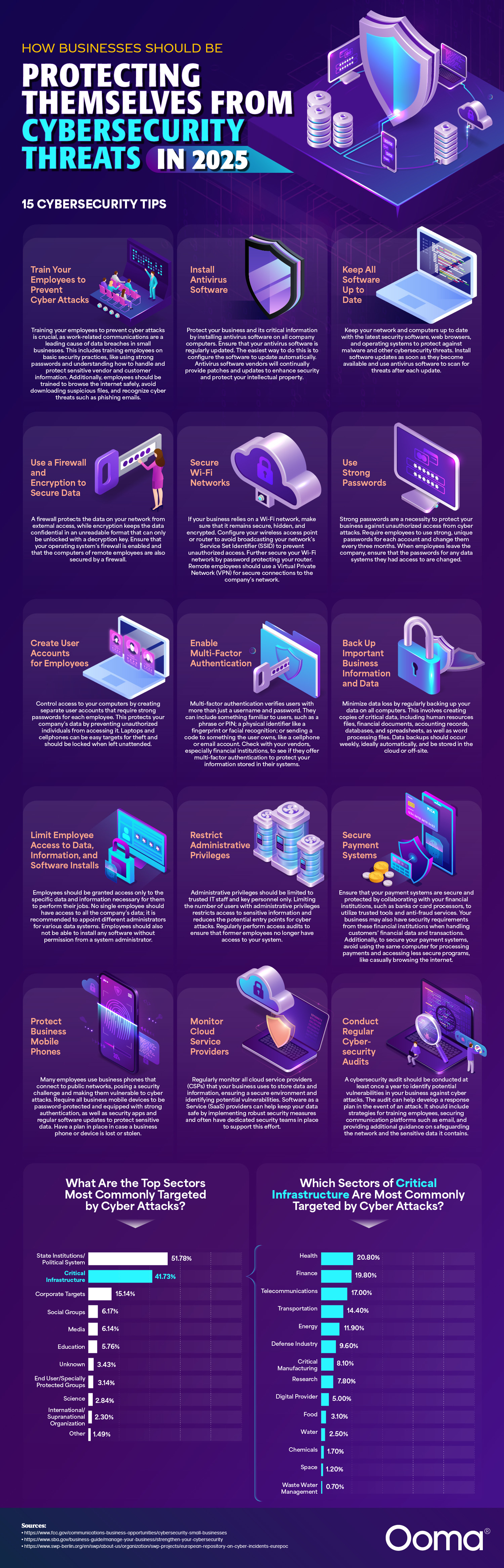
15 cybersecurity tips:
Train your employees to prevent cyber attacks
Training your employees to prevent cyber attacks is crucial, as work-related communications are a leading cause of data breaches in small businesses. This includes training employees on basic security practices, like using strong passwords and understanding how to handle and protect sensitive vendor and customer information. Additionally, employees should be trained to browse the internet safely, avoid downloading suspicious files, and recognize cyber threats such as phishing emails.
Install antivirus software
Protect your business and its critical information by installing antivirus software on all company computers. Ensure that your antivirus software is regularly updated. The easiest way to do this is to configure the software to update automatically. Antivirus software vendors will continually provide patches and updates to enhance security and protect your intellectual property.
Keep all software up to date
Keep your network and computers up to date with the latest security software, web browsers, and operating systems to protect against malware and other cybersecurity threats. Install software updates as soon as they become available and use antivirus software to scan for threats after each update.
Use a firewall and encryption to secure data
A firewall protects the data on your network from external access, while encryption keeps the data confidential in an unreadable format that can only be unlocked with a decryption key. Ensure that your operating system’s firewall is enabled and that the computers of remote employees are also secured by a firewall.
Secure Wi-Fi networks
If your business relies on a Wi-Fi network, make sure that it remains secure, hidden, and encrypted. Configure your wireless access point or router to avoid broadcasting your network’s Service Set Identifier (SSID) to prevent unauthorized access. Further secure your Wi-Fi network by password protecting your router. Remote employees should use a Virtual Private Network (VPN) for secure connections to the company’s network.
Use strong passwords
Strong passwords are a necessity to protect your business against unauthorized access by cyber attackers. Require employees to use strong, unique passwords for each account and change them every three months. When employees leave the company, ensure that the passwords for any data systems they had access to are changed.
Create user accounts for employees
Control access to your computers by creating separate user accounts that require strong passwords for each employee. This protects your company’s data by preventing unauthorized individuals from accessing it. Laptops and cellphones can be easy targets for theft and should be locked when left unattended.
Enable multi-factor authentication
Multi-factor authentication verifies users with more than just a username and password. They can include something familiar to users, such as a phrase or PIN; a physical identifier like a fingerprint or facial recognition; or sending a code to something the user owns, like a cellphone or email account. Check with your vendors, especially financial institutions, to see if they offer multi-factor authentication to protect your information stored in their systems.
Back up important business information and data
Minimize data loss by regularly backing up data on all computers. This involves creating copies of critical data, including human resources files, financial documents, accounting records, databases, customer accounts and spreadsheets, as well as word processing files. Data backups should occur weekly, ideally automatically, and be stored in the cloud or off-site.
Limit employee access to data, information, and software installs
Employees should be granted access only to the specific data and information necessary for them to perform their jobs. No single employee should have access to all the company’s data; it is recommended to appoint different administrators for various data systems. Employees should also not be able to install any software without permission from a system administrator.
Restrict administrative privileges
Administrative privileges should be limited to trusted IT staff and key personnel only. Limiting the number of users with administrative privileges restricts access to sensitive information and reduces the potential entry points for cyber attacks. Regularly perform access audits to ensure that former employees no longer have access to your system.
Secure payment systems
Ensure that your payment systems are secure and protected by collaborating with your financial institutions, such as banks or card processors, to utilize trusted tools and anti-fraud services. Your business may also have security requirements from these financial institutions when handling customers’ financial data and transactions. Additionally, to secure your payment systems, avoid using the same computer for processing payments and accessing less secure programs, like casually browsing the internet.
Protect business mobile phones
Many employees use business phones that connect to public networks, posing a security challenge and making them vulnerable to cyber attacks. Require all business mobile devices to be password-protected and equipped with strong authentication, as well as security apps and regular software updates to protect sensitive data. Have a plan in place in case a business phone or device is lost or stolen.
Monitor cloud service providers
Regularly monitor all cloud service providers (CSPs) that your business uses to store data and information, ensuring a secure environment and identifying potential vulnerabilities. Software as a Service (SaaS) providers can help keep your data safe by implementing robust security measures and often have dedicated security teams in place to support this effort.
Conduct regular cybersecurity audits
A cybersecurity audit should be conducted at least once a year to identify potential vulnerabilities in your business against cyber attacks. The audit can help develop a response plan in the event of an attack. It should include strategies for training employees, securing communication platforms such as email, and providing additional guidance on safeguarding the network and the sensitive data it contains.
What are the top sectors most commonly targeted by cyber attacks?
| Sector | Percentage of all global incidents targeting this sector (1/1/2000–5/28/2025) | |
| 1 | State Institutions/Political System | 51.78% |
| 2 | Critical Infrastructure | 41.73% |
| 3 | Corporate Targets | 15.14% |
| 4 | Social Groups | 6.17% |
| 5 | Media | 6.14% |
| 6 | Education | 5.76% |
| 7 | Unknown | 3.43% |
| 8 | End User/Specially Protected Groups | 3.14% |
| 9 | Science | 2.84% |
| 10 | International/Supranational Organization | 2.30% |
| 11 | Other | 1.49% |
Which sectors of critical infrastructure are most commonly targeted by cyber attacks?
| Sector | Percentage of All Incidents Targeting Critical Infrastructure (1/1/2000–5/28/2025) | |
| 1 | Health | 20.80% |
| 2 | Finance | 19.80% |
| 3 | Telecommunications | 17.00% |
| 4 | Transportation | 14.40% |
| 5 | Energy | 11.90% |
| 6 | Defense Industry | 9.60% |
| 7 | Critical Manufacturing | 8.10% |
| 8 | Research | 7.80% |
| 9 | Digital Provider | 5.00% |
| 10 | Food | 3.10% |
| 11 | Water | 2.50% |
| 12 | Chemicals | 1.70% |
| 13 | Space | 1.20% |
| 14 | Waste Water Management | 0.70% |
Sources
https://www.fcc.gov/communications-business-opportunities/cybersecurity-small-businesses
https://www.sba.gov/business-guide/manage-your-business/strengthen-your-cybersecurity



